Connect any user to any resource
IBM Security Verify allows IT, security and business leaders to protect their digital users, assets and data in a hybrid multicloud world, while enabling technical agility and operational efficiency as a cloud-native solution. Beyond single sign-on (SSO) and multifactor authentication (MFA), Verify is a modernized, modular IDaaS that provides deep AI-powered context for risk-based authentication and adaptive access decisions, guided experiences for developer consumability and comprehensive cloud IAM capabilities, including user management, access recertification campaigns and identity analytics.
Features of IBM Security Verify for Workforce IAM
Log in with federated single sign-on (SSO)
Eliminate username and password hassles and secure access to all your applications with a single set of login credentials. Deliver one-click access to applications from a unified SSO launchpad using out-of-the-box common SaaS application connectors or templates for custom SAML 2.0 or OpenID Connect applications. Read the documentation
Enhance security with multi-factor authentication (MFA)
Protect accounts with an additional security layer and meet compliance requirements with a common approach to MFA across applications, VPN, Windows desktops and Linux. Infuse multiple modern forms of user authentication per resource beyond SMS/email one-time passwords, including passwordless authentication options like IBM Verify mobile app push notifications, user biometrics, QR codes, FIDO2 hard tokens and more. Read the blog
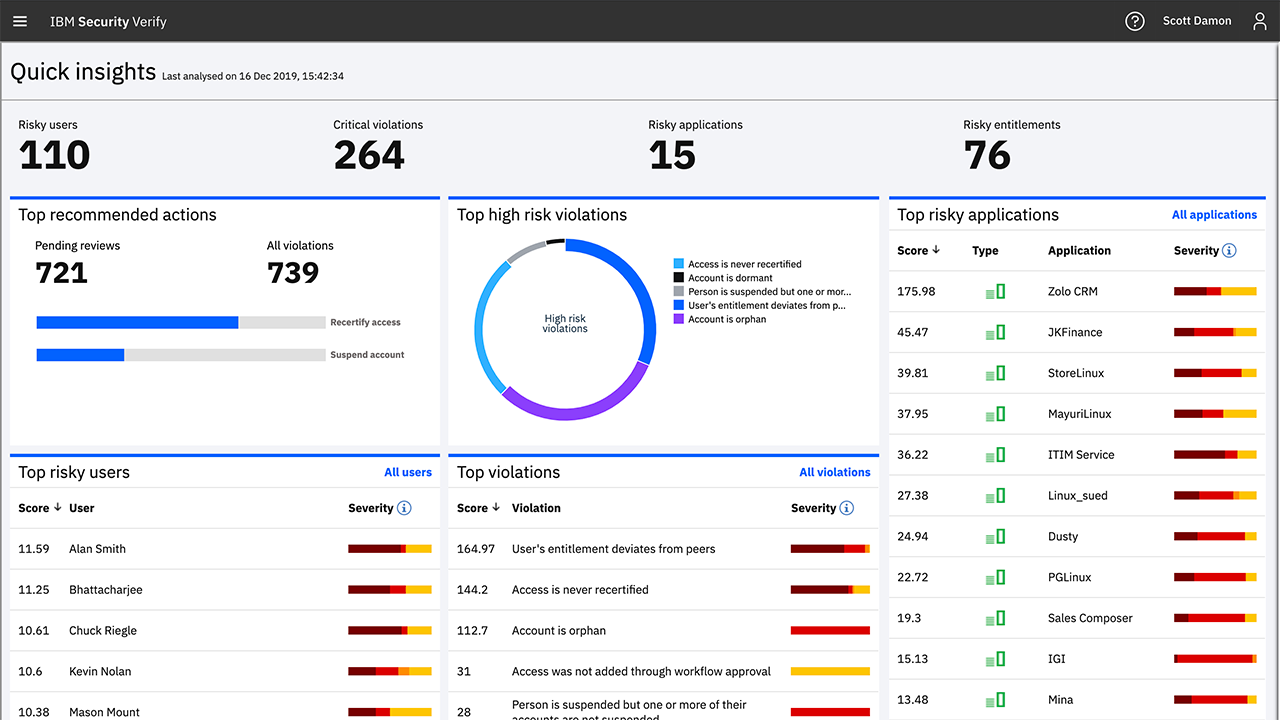
Identify and mitigate access risks with identity analytics
Add risk awareness with a holistic view of identity lifecycle risk including decision support in the form of risk scores for users, applications, and entitlements, accompanied by recommended mitigation actions powered by machine learning. Read the documentation
Adapt for context using continuous access control
Allow streamlined access to low-risk users and either block or challenge access in higher-risk conditions with contextual, risk-based authentication and adaptive access. Organizations can use a simple policy editor to apply AI-informed access policies to prompt for MFA based on deep fraud detection signals across user, device, activity, environment and behavior context. View the demo
Enable user provisioning and lifecycle management
Enable automatic provisioning and deprovisioning for applications with SCIM and provide users with self-service options to request access to applications and reset and manage their own passwords. Connect to existing directories through SAML or identity agents for LDAP and Active Directory, and synchronize user directories with the cloud directory to consolidate a single source. View Knowledge Center
Automate recertification campaigns
Streamline joiner-mover-leaver provisioning processes, and implement a periodic recertification cadence for higher risk applications to meet compliance requirements. View Knowledge Center
Simplify complex user management
Leverage predefined user attribute functions for common adoption and migration needs, call out to third party tools and databases to enrich user profiles with custom attributes, and run multi-line rules and expressions for complex attribute use cases for user management. Read the documentation
Extend SSO to UEM with IBM Security MaaS360 integration
Deliver seamless SSO, and verify users and devices with compliance-based conditional access, for all apps and unified endpoint management (UEM)-enrolled devices. View Knowledge Center
Extend workflows with QRadar and Resilient integration
Infuse identity as a central pillar of any zero trust strategy by integrating with threat management and incident response out-of-the-box. Stream Verify event data to QRadar to identify and analyze threat anomalies, and send Verify anomalies and other events to Resilient to take action, such as automatically resetting a password or removing an entitlement. Get Security Verify Functions for Resilient (link resides outside ibm.com)
Protect on-premises applications from the cloud
Bridge the gap in your IAM infrastructure and simplify your migration to a cloud-based identity provider with a lightweight application gateway that extends access control to on-premises web applications. Read the documentation (link resides outside ibm.com)
Troubleshoot events with custom activity reports
Investigate trends and troubleshoot suspicious events with user and application activity reports, from a global overview down to granular parameters from a single login. Audit all user activity for compliance purposes, view management changes and audit administrative activity, visualize MFA trends or application usage over time and more. View Knowledge Center
Empower managers to control access with delegation
Reduce time and skill dependencies on IT. Delegate the responsibility of application ownership to line of business managers, empowering them to provide their employees with faster access to applications. View Knowledge Center
How customers use it
Assess full user context with Adaptive Access
Problem
Balancing security with user experience, allowing frictionless access to low-risk users.
Solution
Take context into account by infusing risk-based authentication into access policy decisions. Protect against higher-risk conditions without burdening low-risk users.
Monitor identity lifecycle risk with Identity Analytics
Problem
Understanding key risk areas in an IAM environment and what to do about them.
Solution
Scan for top risks across users and applications and leverage recommended mitigation actions powered by machine learning.
Automate access recertification campaigns
Problem
Auditing to ensure access levels remain appropriate over time adds effort and is difficult to keep up-to-date to meet compliance requirements.
Solution
Take an automated approach and set up as many periodic recertification campaigns as you need, at any cadence.
Simplify access requests
Problem
Onboarding employees can be difficult to secure access for all employees appropriately, and IT has too many application access requests to sort through.
Solution
An application catalog and access request interface that lets you provision access to applications faster.
Investigate authentication events
Problem
Lack of insight into user trends, suspicious events, and authentication challenges.
Solution
Dive into user and application reports to identify authentication patterns and investigate suspicious events. Dig into specific users to investigate common issues like SSO activity, account lockouts, login failures, or credential resets.




 Contact us
Contact us 





















