Obrela’s services are transactable on Ingram’s Marketplace, making it easy for the Channel Partner to expand the portfolio and find new growth.
Obrela completes the partner’s cybersecurity offering with simple to communicate, simple to sell, simple to deploy MDR/EDR service. Easily transactable the UK&I Channel Partners can price up, order and deploy MDR or EDR services only a few clicks away in a fully managed model, with no upfront costs and monthly billing in a 12mos term commitment.

Obrela’s Managed Detection & Response (MDR) service for Azure Sentinel combines collective intelligence practices and methods with leading edge security analytics and sophisticated risk management technology to identify, analyze, predict and prevent cyber-security threats in real time. OBRELA expands the sentinel ecosysthme via Azure Lighthouse to deliver a powerful multi-tenant SIEM while data is persisted and analyzed on the Client tenant.
Microsoft Azure Sentinel is a ultra scalable, cloud-native, security information event management (SIEM) and security orchestration automated response (SOAR) solution. Azure Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, proactive hunting, and threat response.
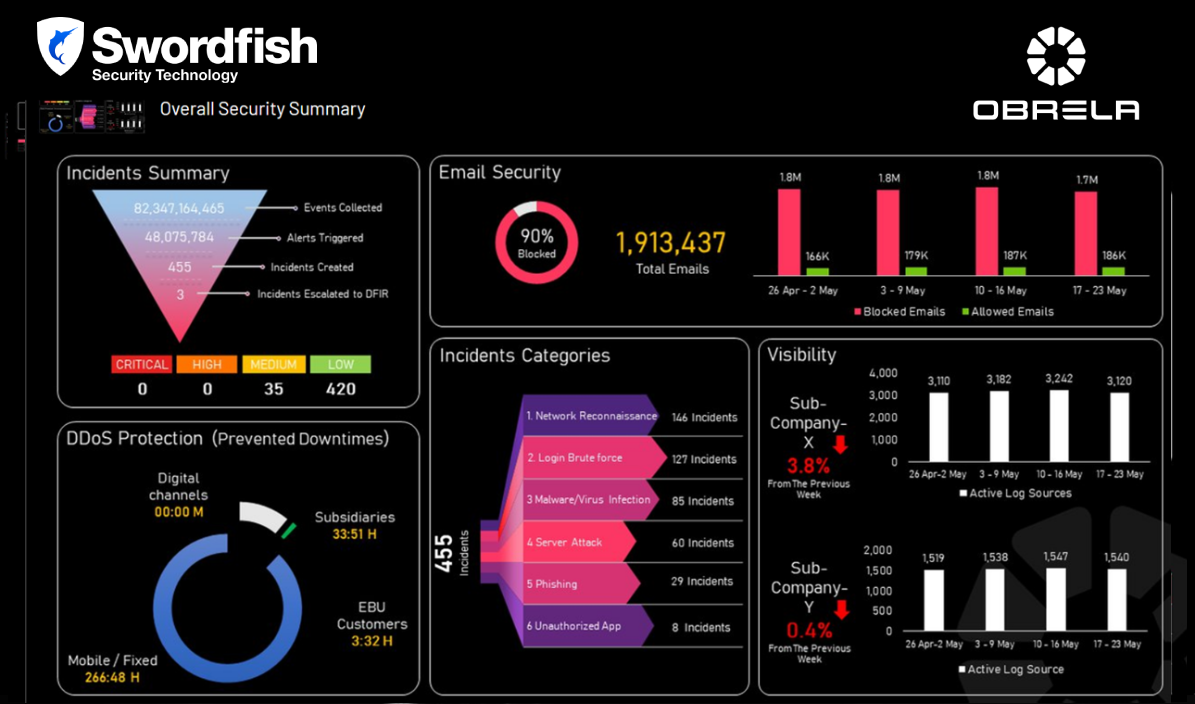
Threat detection analytics, an integral part of the MDR service, collect and analyze structured and unstructured security related data from multiple systems, network devices and other critical assets, generating valuable intelligence for new, emerging and advanced security threats.
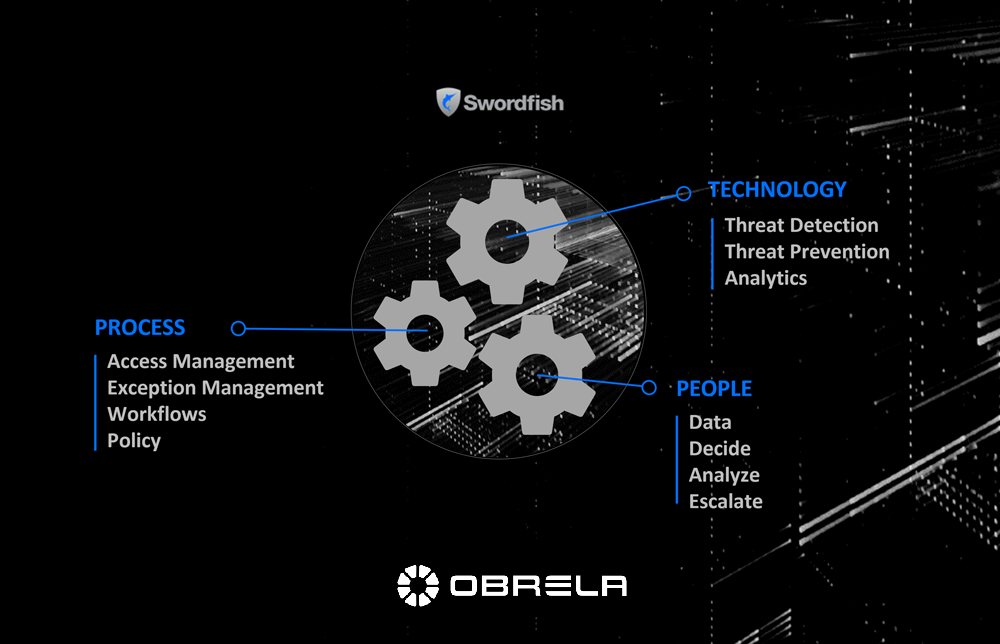
Obrela’s SOC (Security Operations Cener) also an integral part of the MDR service, staffed by threat analysts with IT monitoring expertise provides 24×7 monitoring on site, incident escalation the moment a threat is validated providing to the customers MITRE- like recommendations for fast and effective security incident response.
Key features
Operations and Incident Response Integration with OBRELA 24x7x365 Services including
Integration and Visibility Guide
Enable collection (integration, parsing, categorization) and support for any system or inhouse application that can generate logs.
Use-case-ready approach
Playbooks and Automation OBRELA MDR playbooks running on OBRELA cloud triggered by incidents and alerts, cross-tenant
Why select Obrela – Reseller values
Our clients are offered the advantage of fast integration to OBRELA’s Managed Detection & Response (MDR) service and day one visibility of security threats in their enterprise environment. Clients can build on top customized processes and procedures for risk compliance and incident response plans.
Download the more brochures for more details
IT monitoring Download here
Cloud monitoring Download here
Learn more: https://www.obrela.com/services/managed-threat-detection-and-response/
https://www.obrela.com/it-monitoring/
https://azure.microsoft.com/en-us/services/azure-sentinel/
Start Now Click here
**Download the brochure for more details
Learn more:
OBRELA’s MDR Download here
OT Monitoring Download here
MICROSOFT Azure Download here
MDR in Action:
Oil & Gas Industry Download here
Healthcare Industry Download here
Vessels Download here









 Contact us
Contact us 







