SlashNext Complete™
Multi-channel phishing protection platform for users across email, web, mobile and API. Stop 65% more spear phishing, legitimate service compromise, BEC, rougueware, SMiShing, social engineering and other human compromise attacks in Microsoft 365, Teams, Zoom, Box, SMS, LinkedIn, WhatsApp and other messaging channels.
1. SlashNext Email Protection for Microsoft M365 – AI-Powered Email Security for Microsoft 365
Protect users from targeted credential stealing, supply chain threats, spear-phishing, trusted service compromise, social engineering scams, ransomware, and malware link threats that elude other security solutions up to 65% of the time, according to Tolly Group independent testing.
SEG’s and Other Solutions Miss the Threats that Matter: Spear phishing and other threats often slip past security controls because reputation, URL rewriting and trust graphs are not able to detect phishing hiding on trusted sites. SlashNext AI-powered detection and LiveScan™ sees through evasion tactics and detects previously unknown, zero-hour threats including, compromised websites and trusted hosting service, shortened links. multiple redirects and other types of obfuscation.
2. SlashNext Mobile Protection
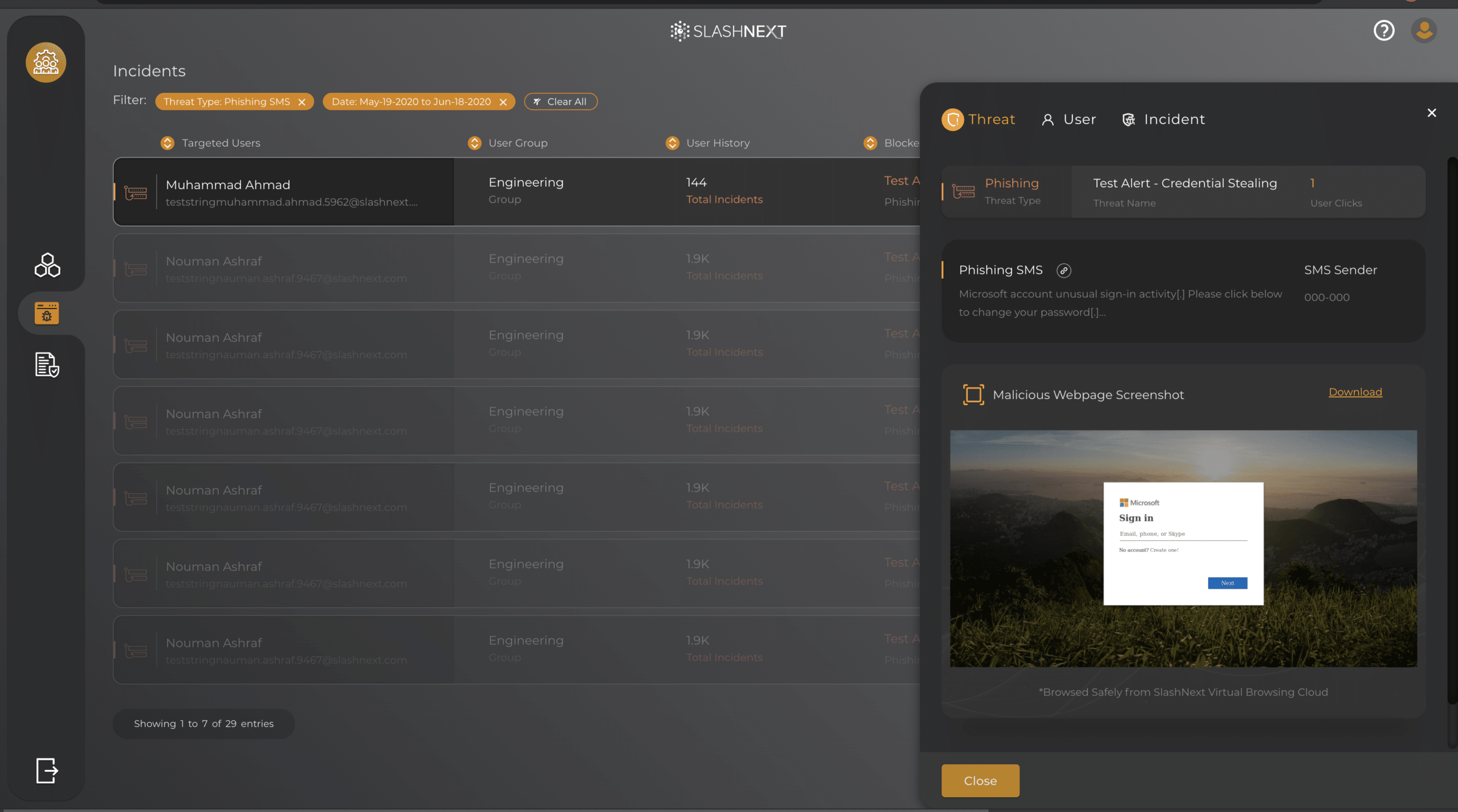
Stop smishing and business text compromise with zero-hour phishing protection against the broadest range of phishing threats in any mobile application.
Solve Complex Mobile Phishing Challenges
Designed to address mobile protection challenges in BYOD and managed device environments.
- Stop smishing and business text compromise using on-device machine learning
- Zero-hour phishing protection for users working anywhere
- Automated phishing protection with on-click training
- Lightweight apps for iOS and Android with no impact on battery consumption or device performance
- Guaranteed Privacy and No PII Risks
- Deploy using any UEM including JAMF and inTune
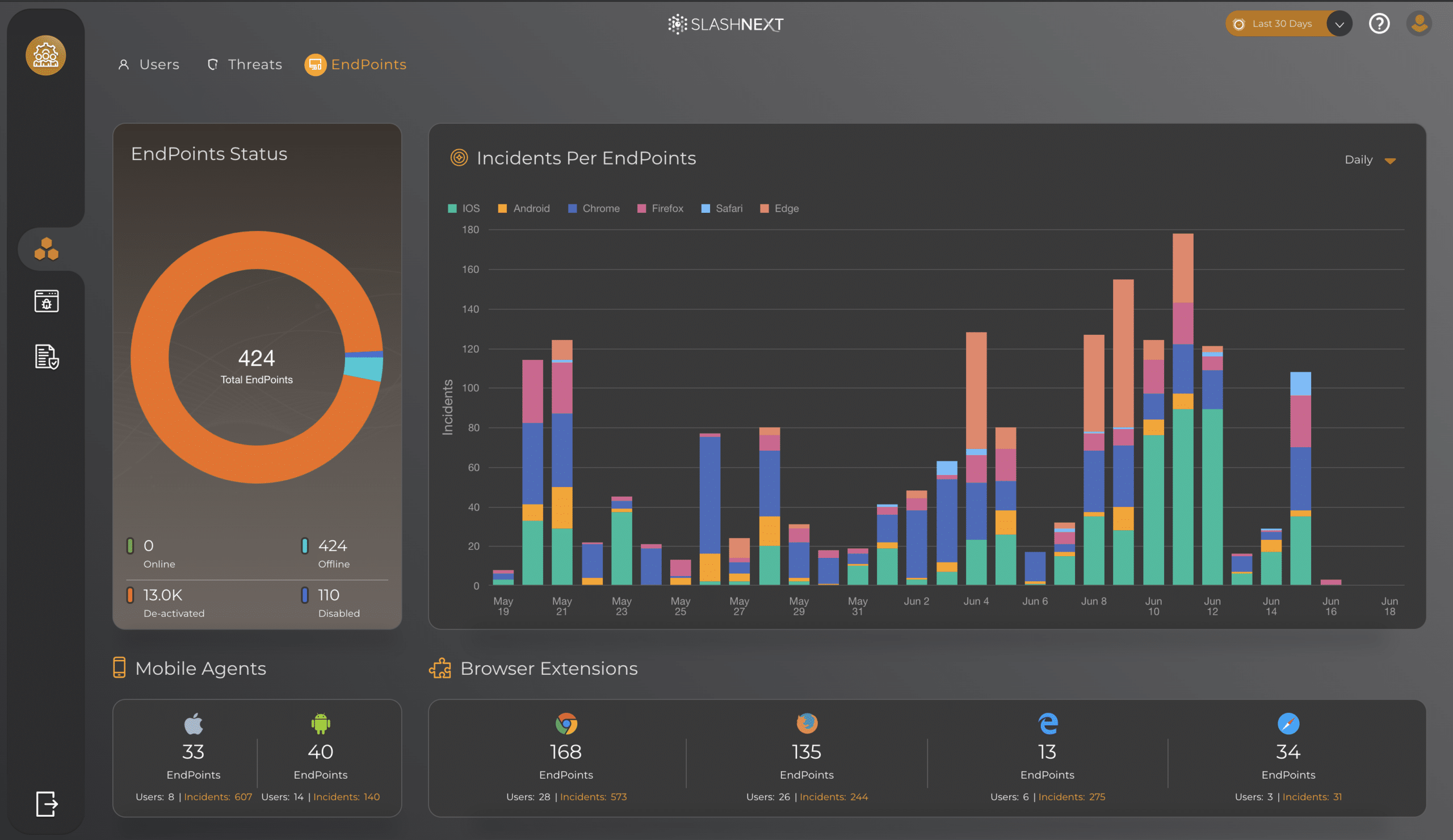
3. SlashNext Endpoint (Browser) Protection
SlashNext’s AI technology provides real-time detection with extreme accuracy that detects malicious site hours and sometimes days before the competition. Protect users from the broadest range of zero-hour phishing sites with cloud-powered browser protection that is better than browser isolation. Available for Chrome, Safari, Edge, Firefox, and more.
Powerful Multi-Vector Protection
SlashNext protects Windows, Mac, Chrome OS, and Linux users from phishing and rogue browser extensions regardless of which attack vector is used—email, ads, social media, search, collaboration platforms, and more.
By blocking phishing sites in real-time, SlashNext protects users from more phishing threats including those that evade multi-layer enterprise defenses.
- Credential Stealing: The act of attaining passwords with the intent of accessing protected data.
- Spear Phishing: Targeted attack to gain access to an individual’s account or impersonate a specific individual.
- Bank Fraud: Social engineering tactics to obtain money, assets or other property held by an organization.
- Social Engineering: Using deception to manipulate users into divulging confidential information for fraudulent use.
- BEC, ATO and Supply Chain Attacks: Targets executives or financial teams to defraud a company for financial gain.
- Rogueware and HTML Attachments: Intended to inject code, take-over browser canvas or download malware.
- Smishing and Business Text Compromise: Using text messages to trick users into divulging passwords or other PII for fraudulent use.
- Trusted services compromise: Commonly used to launch phishing attacks or hack other trusted domains.




 Contact us
Contact us 



