Many organizations are now embracing the use of smartphones and tablets to increase productivity in the workplace, and as more sensitive data goes mobile, your organization’s security policies must extend to your mobile endpoint devices. Lookout Mobile Endpoint Security makes it easy to get visibility into the entire spectrum of mobile risk, apply policies to measurably reduce that risk, and integrate into your existing security and mobile management solutions.
How It Works
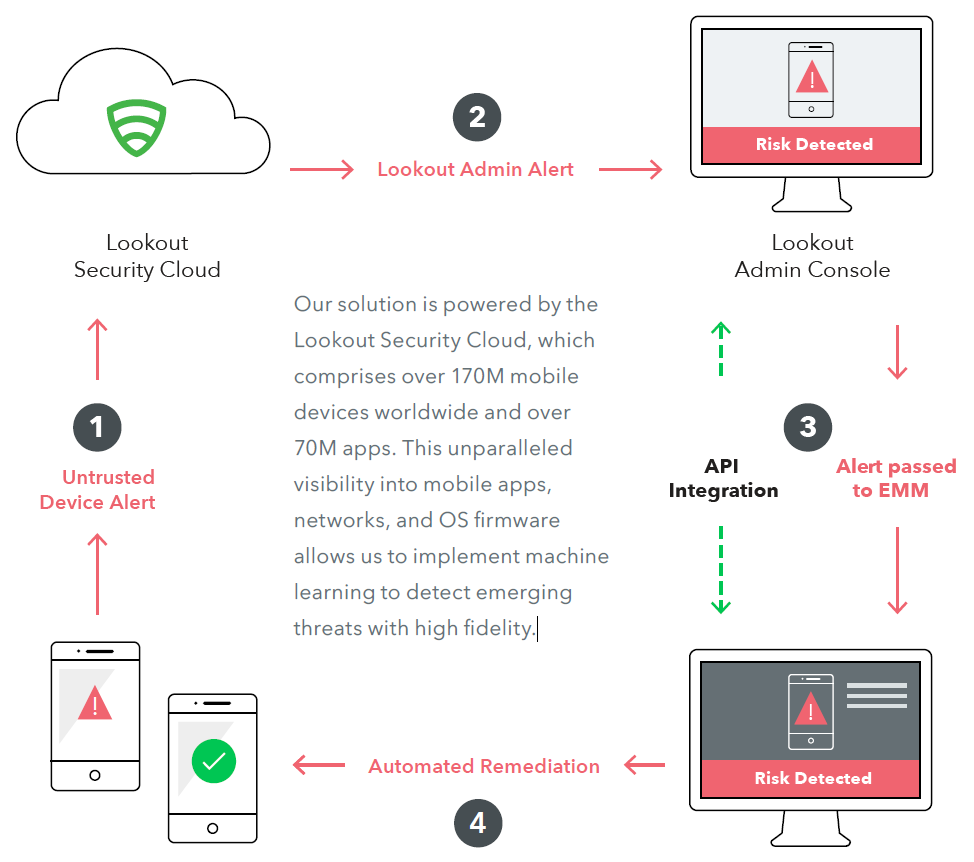
Lookout Mobile Endpoint Security leverages a lightweight endpoint app on employee devices, a cloud-based admin console that provides real time visibility into mobile risk, and integration with leading Enterprise Mobility Management (EMM) solutions.

Benefits
Measurable reduction of risk
Close a large security gap and measure your risk reduction with Lookout’s analysis and reporting features
Seamless interoperability
Lookout integrates with all SIEM systems via our Mobile Risk API, including Splunk, Windows Defender ATP, Micro Focus, ArcSight, IBM Security and QRadar
Visibility into mobile incidents
Get real-time visibility into incidents on mobile devices, so you can respond quickly and effectively
Securely enable mobility
Embrace more flexible mobility programs, including BYOD, to increase employee productivity and stay competitive
Privacy by design
Ensure your data sovereignty and employee privacy policies are upheld using our privacy controls features
Easy to deploy and maintain
We integrate with any EMM (such as VMware Workspace ONE® UEM, Microsoft Intune, BlackBerry® UEM, IBM MaaS360®, and MobileIron) for simple deployment and management
Mobile Endpoint Security for Threats
As more sensitive data is accessed by mobile devices, they are increasingly becoming a target for attackers. Lookout Mobile Endpoint Security identifies mobile threats targeting these primary attack vectors:
- App-based threats: Malware, rootkits, and spyware
- Network-based threats: Man-in-the-middle attacks
- Device-based threats: Jailbroken/rooted devices, outdated OS, risky device configurations
- Phishing and content threats: Protect against any phishing attempt via email, social media apps, SMS text or websites
.png)









 Contact us
Contact us 



